Although SSL/TLS certificates provide nice security, there's still a weak link in this chain: the first request.
When the browser performs the request to your server, the browser has to check the validity of the SSL certificate. This process is known as OCSP (Online Certificate Status Protocol). As you can imagine, this may lead to a higher response time, as the browser needs to validate the certificate on the client-side.
Furthermore, this leads to a privacy issue: The Certificate Authority (CA) knows what website is being accessed and who accessed it.
Luckily, we have a way of improving this process: we can configure our servers to perform the OCSP, and just send the browser a time-stamped OCSP response from the CA. This would eliminate the need of validating the certificate on the client-side, speeding up, and securing the first connection to your website.
What are the main advantages of enabling OCSP Stapling?
- Guaranteed security and privacy of user data
- Increased protected content download speed as browsers do not need to make additional requests
- Secured bandwidth on the client-side, which would be an advantage for mobile users
- Make your website more trustworthy and improve the delivery speed of protected content
Enabling OCSP Stapling in Plesk
The latest version of Plesk made it super easy to enable OCSP Stapling. You just need to go to your website panel:
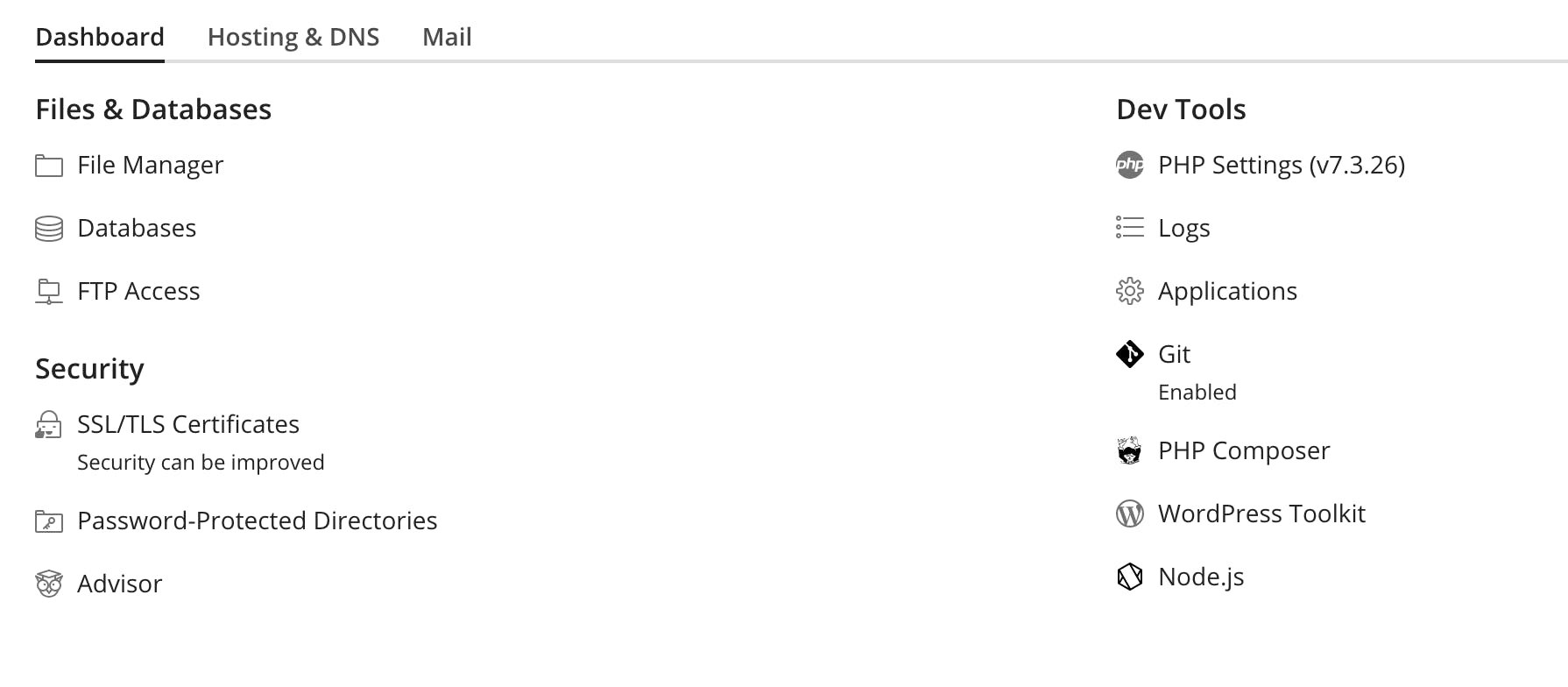
Once there, click on SSL/TLS Certificates, and enable OCSP Stapling on the left pane:
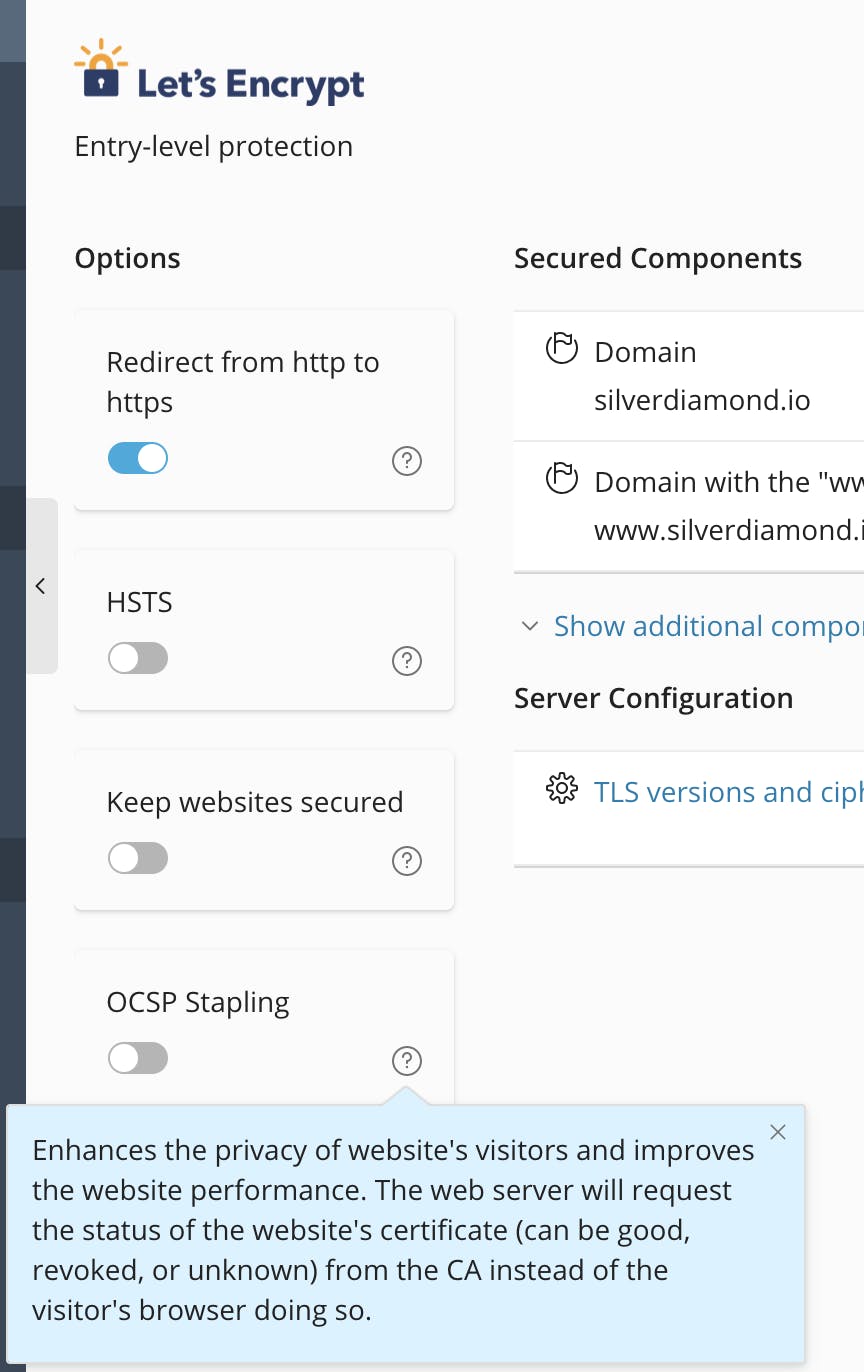
That's it! 🥳
If you are using an older version of Plesk, you can still enable OCSP Stapling using a workaround:
- Connect to your server via SSH
- Add following records to
/etc/sw-cp-server/conf.d/ssl.conf
ssl_stapling on;
ssl_stapling_verify on;
resolver 8.8.4.4 8.8.8.8 valid=300s;
resolver_timeout 10s;
Enabling OCSP Stapling in AWS
AWS Cloudfront supports OCSP Stapling since 2014. Luckily, we don't need to perform any additional setting to our CloudFront, as it's enabled by default 🎉.
Manually configuring OCSP Stapling in Nginx and Apache
Our friends at Digital Ocean have written a super nice post on how to manually configure OCSP Stapling both in Nginx and Apache servers.
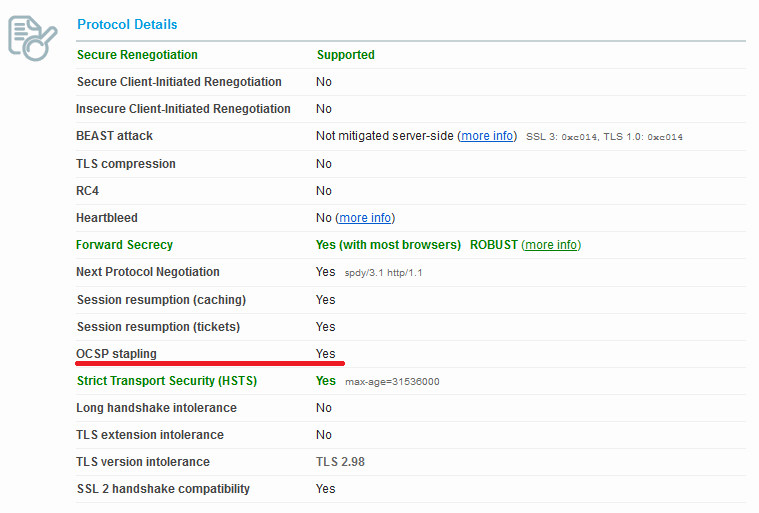
Checking if our OCSP Stapling is correctly setup
To check this online, go to SSLLabs and run the analysis. Once it's over (it can take a while), you can check it under the Protocol Details section:
Summary
We've seen how to enable OCSP Stapling and how this small setting can really improve the speed and security of our website. See you in the next post! 🤩

